Businesses are constantly grappling with the complexities of data privacy today. Regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have made data protection a top priority given the legal implications for non-compliance. Sadly, cybercriminals are taking advantage of this focus, launching sophisticated phishing scams that leverage data privacy concerns to trick individuals into compromising their security.
Here’s a look at a recent phishing email scam that plays on people’s data privacy concerns associated with regulations like GDPR and CCPA — and why your business should be on high alert.
A New Wave of Email Phishing Attacks
Below is a phishing email posing as a notice about the sale or sharing of personal data. At first glance, the email appears to be a legitimate communication, warning recipients about data sharing practices and providing options to “opt-out.” Yet, upon closer inspection, several red flags indicate it’s a scam.
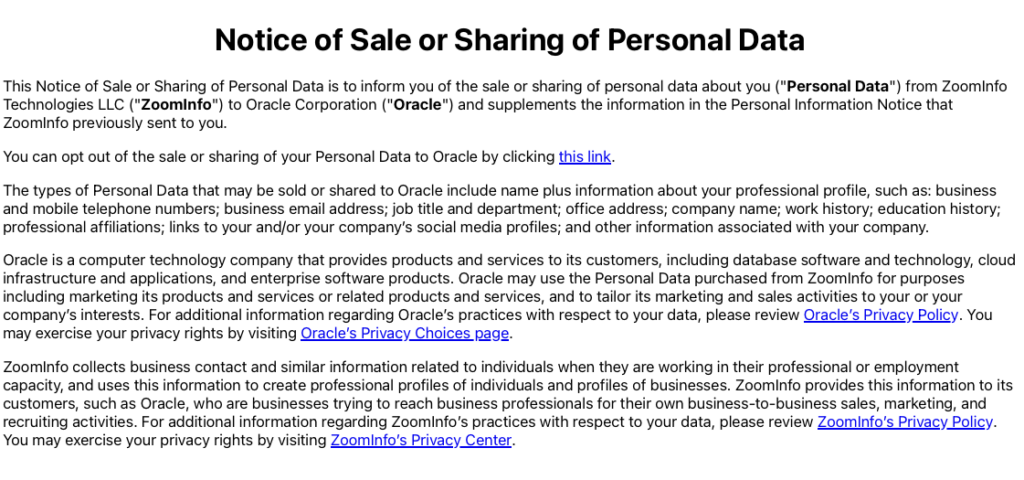
The purpose of this type of email phishing attack is to confirm that your email address is valid and there’s a human behind it. While the informational links go to legitimate organizations’ websites (Oracle & Zoominfo), the “opt-out” link takes you to a page that is not on the official Oracle domain. Instead, it is the same GoDaddy-registered domain that the phishing email originates from. The email’s suggestion that your personal data will be sold is simply attempting to scare you into action. When in doubt, delete the email or report it to your IT team without clicking on any links.

Some general red flags to watch out for that could signal a potential phishing scam include:
- Generic Greeting – Legitimate organizations that have your data legally, especially when they’re contacting you regarding data privacy concerns, will typically address you by your full name or company name. Be suspicious of emails that begin with a vague “Dear customer” or lack personalization.
- Mismatched URLs – Hover over any links embedded in the email without clicking on them. This will allow you to see the actual URL. If it doesn’t match the URL of the company’s official website or seems suspicious in any way, it’s likely a phishing attempt.
- Urgent or Threatening Language – Phishers often use scare tactics, urging recipients to act immediately to avoid some form of consequence. Language that creates a sense of urgency or fear can be a sign of an email phishing scam.
- Spelling and Grammar Mistakes – Professional organizations typically proofread their communications. Be on the lookout for glaring spelling, punctuation, or grammar errors, which are common in email phishing.
- Request for Personal Information – Legitimate organizations will not ask for sensitive data over email. Do not disclose sensitive data like passwords or Social Security numbers electronically or if anything seems suspicious.
- Odd Sender Email Address – Even if the sender’s name looks correct, an odd email address (especially one that is overly complex or deviates from the official domain of the supposed sender) can be a red flag.
- Inconsistencies in Formatting – Pay attention to unusual fonts, mismatched logos, or email layouts that don’t seem to align with official communications from the supposed sender. Something as simple as a curve on the edge of the letter “n” in a brand logo could be a red flag.
- Lack of Transparency – Authentic GDPR or CCPA-related emails should provide clear information about why you’re receiving the message and how your data is being used. Vague descriptions or a lack of detail can be cause for suspicion.
When in doubt, trust your instincts first. If something feels off about an email, it’s better to verify its authenticity directly with the organization before taking any action.
Risks of Email Phishing Scams
Phishing emails like the above example are designed to exploit human psychology. They’re designed to tap into our fears, urgencies, or simple curiosity and trick us into clicking malicious links or providing sensitive information. Here’s why they’re so dangerous:
- Malware Installation – Clicking on embedded links or downloading attachments from phishing emails can introduce malware into your system, leading to data breaches or system failures.
- Credential Theft – Cybercriminals use deceptive web pages that mirror legitimate sites to capture your login credentials, then gain unauthorized access to sensitive data.
- Financial Loss – Successful email phishing attacks can lead to unauthorized financial transactions, with victims losing significant amounts of money.
The Rise of Cyber-Attacks

The frequency and sophistication of cyber-attacks have been on the rise. Cybercrime damages are predicted to hit $8 trillion annually in 2023, underscoring the importance of being vigilant and proactive in cybersecurity efforts.
So how do you protect your business from these dangers? Here are some steps to take as a start:
- Educate Employees – Regularly train employees to recognize phishing emails and the dangers associated with them.
- Verify Email Sources – Always verify the legitimacy of unexpected or suspicious emails, especially those that call for immediate action.
- Update Systems – Keep your operating systems, software, and applications regularly updated to benefit from the latest security patches.
- Implement Advanced Security Measures – Use advanced email filtering solutions, two-factor authentication, and other security protocols to add extra layers of protection.
These efforts are just a starting point. It’s incredibly important to consult with cybersecurity professionals that specialize in protecting companies from these types of attacks.
Always Be on the Lookout for Phishy Emails
Pun intended. In the face of growing cyber threats, staying informed and proactive is key. Remember, cybercriminals are constantly evolving their tactics, leveraging concerns like GDPR and CCPA to exploit vulnerabilities. Make sure to be diligent, continuously updating your cybersecurity strategies and ensuring that your employees are well-equipped to identify and respond to threats.
